When an application is being created, the Compiler will compile the application source code into several object files made of machine language code. Then the object files are linked together to create the final executable. But as you can see the file is unprotected and can be easily cracked.

Dissembler or De-Compiler:-In the same manner that the source code of an application is converted into machine code at compilation time, there are tools that can convert a compiled application into assembly language or a higher programming language. These tools are known as dissemblers and de-compilers.
An attacker can use a dissembler or de-compiler to study how a specific application works and what a specific routine does. When the attacker has a good knowledge of the target application, he can modify the compiled application to alter his behavior. For example, the attacker could bypass the routine that checks for the trial period in an application and make it run forever or even worse, cause the application to behave as if it was registered.

Software Protectors:-
Software protectors are created to keep an attacker away from directly inspecting or modifying a compiled application. A software protector is like a shield that keeps an application encrypted and protected against possible attacks.
Advantages of using a Software Protector are:
- Protect an application against piracy.
- Prevents attackers from studying how an application is implemented.
- Will not allow attackers to modify an application to change its behavior .
Since software protectors were born, many attackers have centered most of their efforts on attacking the software protectors themselves instead of the applications. Many tools have been developed that aid in the attacking of software protectors. These attacks often result in the attacker obtaining the original application that is decrypted and has the protection wrapper removed.
The main problem with software protectors is that they use protection techniques very well known by crackers, so they can be easily bypassed with traditional cracking tools.

More Effective Solutions:-
Few more things or protection can be added to make the file more safe like garbage code, thread engine etc.
Garbage Code:-
Garbage code should be mixed with the real code in an algorithm. After doing so, an attacker is forced to deal with lots of garbage code when trying to study a specific routine. For example, if an attacker views a disassembled application, they will have to study 8,000 instructions instead of the original 1,000 instructions.
Some software protectors use this technique but use a restricted set of garbage code to be mixed with the real code, so an attacker can easily differentiate which code is real and which is not. The garbage code should be like the real code to make cracking difficult.
Click image to see Clearly.


Secure Entry Point:-
When an application is going to be protected, protecting softwares removes the entry point of the application, the first instructions that are executed in an application, and overwrites them with garbage code. If an attacker finds the application entry point, he will only get the garbage code.

Monitor Blocker:-
Most of the current protectors offer file or registry monitors detection techniques, like finding a specific window class name registered in the system or detecting a specific executable running in memory. An attacker can easily bypass these techniques if he has custom file or registry monitors. A protected application should show this message if a monitoring program is found in memory.

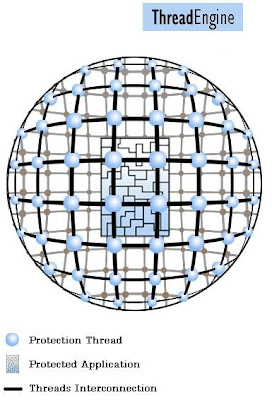
Thread Engine:-
ThreadEngine is a powerful technique that supervises and protects an application at runtime. ThreadEngine is composed by a "web" of threads that work cooperatively with the protected application threads as a single unit. If an attacker threatens a thread, a neighboring thread will report an alert message to the rest of the threads thus exiting the application from memory or executing a customized routine to stop the attacker.
Only a few software protectors use a similar technique, but they do not use a strong communication protocol between each thread and the protected application threads. In this scenario, each thread runs independently making it easy for an attacker to attack each thread to bypass this protection technique.
Anti Dumping:-
Most of the current software protectors use very weak techniques against memory dumpers such as destroying the executable header at runtime. These techniques can easily be bypassed with newer dumping tools.
Non protected Application Image.

Protected Application image

For more info read my post "Importance of File Packers, to visit click here
For more info read my post "Cracking and how to defend it Part I", to visit click here
For more info read my post "Cracking and how to defend it Part II", to visit click here